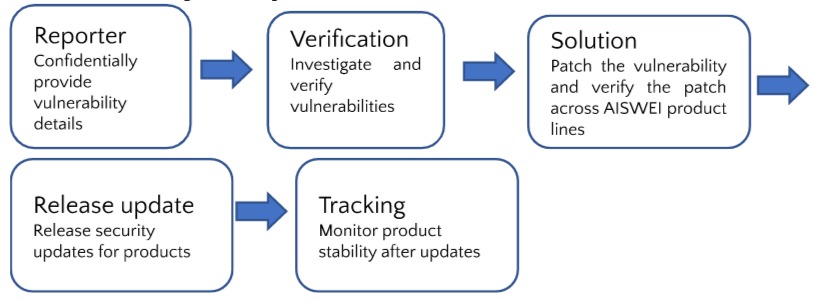
Vulnerability Response and Disclosure Process
Report Vulnerability
You can report security vulnerabilities you find in the following ways
Email
Safety@solplanet.net
Submit Vulnerabilities Online
Response Time
We will verify within 3 working days upon receipt of the report and conduct an initial assessment. The assessment will be completed within 7 working days, and the vulnerability will be patched or a remediation plan will be developed.
Critical risk vulnerabilities will be patched within 7 working days after the assessment is completed. High and medium risk vulnerabilities will be fixed within 30 working days. Low-risk vulnerabilities will be fixed within 180 working days. Please note that some vulnerabilities are dependent on environment or hardware. The final response time will be determined according to the actual situation.
Product Security Update Support Cycle
To protect our customers, AISWEI will provide at least 3 years of security update support for IOT products. If you believe you have discovered a security or privacy vulnerability affecting AISWEI equipment, software, services or web servers, please report it to us. We welcome anyone to report issues, including security researchers, developers, and customers. AISWEI will quickly and carefully address security vulnerabilities in our products.
Vulnerability Level Rating Criteria
The following issues are not vulnerabilities:
1. Bugs that do not involve security issues. Including but not limited to product functional defects, garbled web pages, confusing styles, static file directory traversal, application compatibility and other issues.
2. Vulnerabilities that cannot be exploited. CSRF without sensitive operations, meaningless abnormal information leakage, intranet IP address/domain name leakage.
3. Other problems that cannot directly reflect the existence of vulnerabilities. Including, but not limited to, issues that are pure guesswork.
Low Risk Vulnerabilities:
1. Vulnerabilities that can have certain impact but cannot directly obtain device permissions and affect data security, such as: non-important information disclosure, URL redirection, difficult-to-use XSS security vulnerabilities, common CSRF vulnerabilities.
2. Ordinary unauthorized operation. Including but not limited to incorrect direct object references.
3. Common logic design flaws. Including but not limited to SMS verification code bypass, email verification bypass.
Medium Risk Vulnerabilities:
1. The vulnerability of directly obtaining user identity information. Including but not limited to stored XSS vulnerabilities;
2. Arbitrary text operation loopholes. Including but not limited to any file reading, writing, deleting, downloading and other operations;
3. Unauthorized access. Including, but not limited to modifying user data, and performing user operations by circumventing restrictions;
High Risk Vulnerabilities:
1. Vulnerability of directly obtaining business server permissions. Including but not limited to arbitrary command execution, uploading webshell, arbitrary code execution, command injection, remote command execution;
2. Logical loopholes that have direct and serious impacts. Including but not limited to any account password change vulnerability;
3. Vulnerabilities that can directly steal user identity information in batches. Including but not limited to SQL injection;
4. Unauthorized access. Including but not limited to bypassing authentication to directly access the administrator back end, and weak passwords in the back end.
Critical Risk Vulnerabilities:
1. Direct access to core system permissions. Vulnerabilities that can directly endanger the intranet, including but not limited to: command execution, remote overflow and other vulnerabilities;
2. Vulnerabilities that can obtain a large number of core user data;
3. Logical loopholes that have direct and serious impacts. Vulnerabilities include but are not limited to: serious logic errors, loopholes that can obtain a large amount of benefits and cause losses to companies and users.